The Ethernet LAN has
many security weaknesses when facing attacks externally and internally.
Security measures must be taken to ensure an secured environment for
communications ever the Ethernet LAN. The following are some key risks in an
Ethernet LAN:
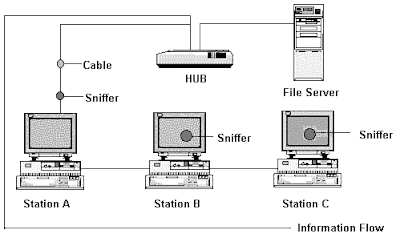
• The primary
weakness with Ethernet is that it is a broadcast system . Every message sent
out by any computer on an Ethernet LAN segment reaches all parts of that
segment and potentially could be read by any computer on the segment. Sniffing
type programs can record, read and analyze all the messages on a segment.
Actually others can read your password and subsequently login to any account.
They can also change the information and forge totally different messages.
• Peer-to-Peer
networking systems (both Windows and Macintosh AppleTalk) for Workgroups allow
people on the network to share files and printers, which open up your files to
anyone using another computer in the group.
• Some applications,
such as FTP program which allows you to get files from and send files to
another computer, may have an option in their configuration which allow other
computers to get into your computer and have access to your files while the
program is running .
• Privileges of the
operating system of a server in the Ethernet maybe incorrectly configured and
users may have unintentional access to sensitive parts of the file store.
• If the NFS
(Network File System) is deployed in an Ethernet LAN and the NFS part of a file
store on a remote computer, the contents of the files can be snooped when
reading or writing a file to the NFS drive.
• It is relatively
easy in an Ethernet LAN to fake an Email message and other messages which
purports to come from someone else. It is also possible to forge a login
session by recording a legitimate one and running the recording later on.
There are many
hardware and software solutions to address the above Ethernet LAN security
issues:
Hardware Solutions
for Ethernet LAN Security
• Use a switched
network: A switch can segregate a network into many parts which can effectively
preventing snooping and sniffing on a network. These switches also reduce network
traffic by limiting messages to only the parts of the network on which they are
needed to improve the efficiency of the whole network.
• Bridges and
Routers: Bridges and routers are electronic filters which only pass a network
message through themselves if the destination lies on the other side of the
filter. Consequently if "the snooper" is on one side of a bridge or
router they will not see any traffic passing between computers on the other
side of the filter.
• LAN Security
Architecture (LSA): a proprietary technique where twisted pair hubs inspect
incoming messages and will only transmit them unscrambled to the destination
computer. All other computers on the hub receive scrambled messages.
Software Solutions
for Ethernet LAN Security
• Encryption: Encrypting
the data passing between your computer and its destination. There are many
encryption technologies and product available which effective protect
information and data privacy. The popular encryption methods used are PGP
(Pretty Good Privacy).
• Authentication:
Use user name and password to authenticate users. It is necessary to encrypt
the password and implement timestamps making forgery extremely difficult.
• Combination
technologies: Many new technologies are available which doing both authentication
and encryption. One of such technologies is Kerberos which uses tokens,
timestamps, tickets and encryption to make transactions between computers
secure.
Many network
security technologies at the layer 3 (the network layer) can also be deployed
to address the Layer 2 (Ethernet layer) security vulnebilities.
Now try to Answer these question
to test your knowledge :
Give two hardware solutions for Ethernet LAN security.
Give two software solutions for Ethernet LAN security.
Please answer these question in a
comment.

No comments:
Post a Comment